
BLE vulnerability may be exploited to unlock cars, smart locks, building doors, smartphones
A Bluetooth Low Energy (BLE) vulnerability may be exploited to unlock Teslas, other cars, smart locks, building access systems, smartphones.

A Bluetooth Low Energy (BLE) vulnerability may be exploited to unlock Teslas, other cars, smart locks, building access systems, smartphones.
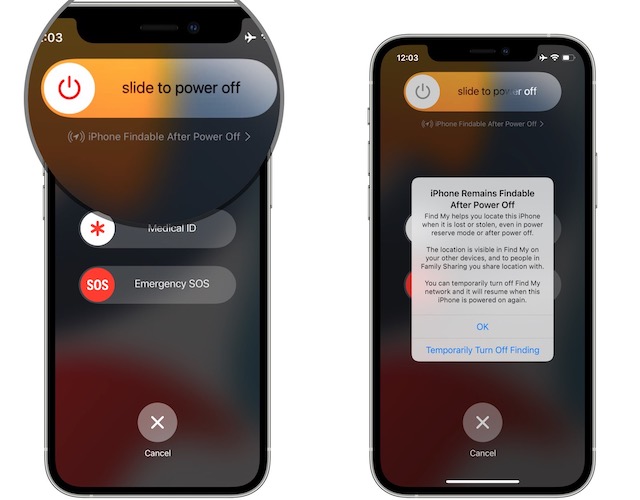
Wireless features Bluetooth, NFC and UWB stay on even when the device is powered down, which could allow attackers to execute pre-loaded malware.

Vendors are patching and deploying fixes for six different vulnerabilities in Bluetooth Core and Mesh specifications allowing MiTM attacks.
Attackers could abuse vulnerabilities discovered in the Bluetooth Core and Mesh Profile specifications to impersonate legitimate devices during the pairing process and launch man-in-the-middle (MitM) attacks.
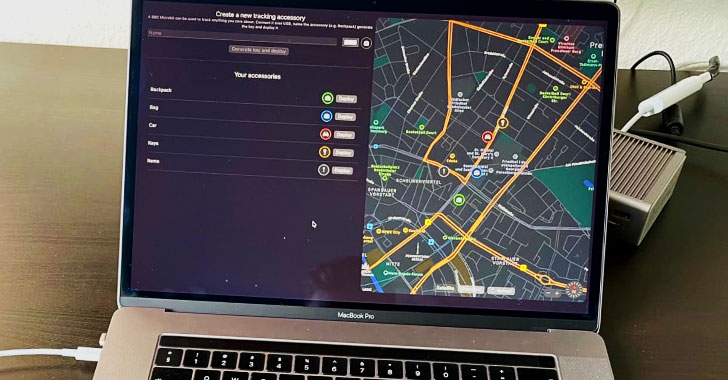
Experts Detail How Apple’s Crowd-Sourced Bluetooth Location Tracking System Could Have Exposed Users Location Reports.

A team of academic researchers have discovered a Bluetooth Low Energy (BLE) vulnerability that allows spoofing attacks that could affect the way humans and machines carry out tasks. It potentially impacts billions of Internet of Things (IoT) devices, researchers said, and remains unpatched in Android devices.